Protecting Yourself in the Digital Age
Introduction
In the current digital environment, email is a crucial communication tool. Yet, it has also turned into a major channel for cybercriminals to initiate phishing attacks. Phishing, a fraudulent strategy, tricks individuals into revealing sensitive data such as login credentials or financial information. The consequences of these attacks can be severe for both individuals and organizations, resulting in financial loss, identity theft, and data breaches. With the growing complexity of phishing tactics, it is increasingly vital to comprehend and apply effective measures for phishing prevention and email security.
In this blog post, we'll explore effective ways to recognize phishing emails, protect against them, and promote safe email practices.
Recognizing Phishing Emails
Phishing emails often employ social engineering tactics to manipulate recipients into responding. Phishing emails often mimic legitimate communications from trusted entities. Here are some common tactics and suspicious elements to look out for:
Urgent Requests: Phishing emails frequently create a sense of urgency, pressuring you to act quickly to avoid negative consequences. They may threaten account suspension or legal action if you don't respond quickly. For instance, they might threaten to suspend your account unless you verify your information within 24 hours.
Generic Greetings: Phishing emails often use generic greetings, like "Dear Customer," instead of your actual name, which is a red flag.
Spoofed Sender Addresses: Verify the sender's email address. Phishing emails often come from addresses that look similar to, but are not exactly the same as, the legitimate source. Attackers often use email addresses that closely resemble legitimate ones. Consider receiving an email from "support@amazo-n.com" rather than "support@amazon.com."
Suspicious Links and Attachments: Phishing emails often include attachments or links that install malware or lead to fake websites designed to steal your information. Always hover over links to see the actual URL before clicking, and be wary of unexpected attachments. Links might appear to lead to legitimate sites but actually direct you to malicious websites.
Unusual Requests: Legitimate companies rarely ask for sensitive information via email. Be wary of emails requesting passwords, social security numbers, or credit card details.
Poor Grammar and Spelling: Many phishing emails originate from non-native English speakers and contain noticeable grammar and spelling errors.
It's crucial to verify links and attachments before clicking or downloading. If you're unsure about an email's authenticity, contact the supposed sender directly using verified contact information.
Protecting against phishing attacks
It is advisable to adopt the following strategies to strengthen your defenses against phishing attacks::
Email authentication protocols:
The SPF (Sender Policy Framework) specifies which mail servers can send emails on your domain's behalf.
DKIM (DomainKeys Identified Mail) enables you to add a digital signature to your emails, thereby verifying their integrity.
DMARC (Domain-based Message Authentication, Reporting, and Conformance): builds on SPF and DKIM by specifying how to handle emails that fail authentication and providing reports on potential phishing attempts.
By verifying the sender's identity, these protocols help prevent email spoofing.
Spam Filters and Anti-Malware Software: These tools can automatically detect and block malicious emails before they reach your inbox.
Strong, Unique Passwords and Two-Factor Authentication (2FA): Use complex passwords and enable 2FA to add an extra layer of security to your accounts. This adds an extra layer of security by requiring a second form of verification in addition to your password.
Educating users about safe email practices
Education is a powerful tool in the fight against phishing. Regularly train employees and users on how to recognize phishing attempts and the importance of not clicking on suspicious links or attachments. Here are some strategies to foster a security-minded culture:
- Regular Cybersecurity Training: To keep employees informed about the latest phishing tactics and safe email practices, conduct regular training sessions. Example: Conduct phishing simulation exercises to test and improve user awareness.
- Creating a Security-Minded Culture: Foster a culture of vigilance in which employees feel responsible for the organization's cybersecurity. Promote best practices, such as verifying email senders and not sharing sensitive information via email.
- Reporting Suspicious Emails: Encourage users to report any suspicious emails to the IT department or service providers for further investigation.
Tools for Filtering Out Malicious Emails
Several email security solutions can help protect against phishing attacks by using machine learning and threat intelligence.
- Microsoft Office 365 Advanced Threat Protection offers real-time protection against malicious links and attachments and uses machine learning to detect phishing attempts.
- Google Workspace Security: Provides robust spam filtering and phishing protection, leveraging Google's extensive threat intelligence.
- Proofpoint uses advanced threat detection to block phishing emails and provides detailed reporting and analytics.
These tools have proven successful in many organizations by significantly reducing the number of phishing emails that reach users' inboxes, thereby lowering the risk of successful attacks.
Best Practices for Safe Email Use
- Verify Before Trusting: Always verify the authenticity of an email, especially if it requests sensitive information or seems unusual. Contact the organization directly using their official website's contact information.
- Be cautious with links and attachments. Avoid clicking on links or downloading attachments from unknown or unexpected emails. When in doubt, contact the sender directly to confirm its legitimacy.
- Use Strong, Unique Passwords: For each account, ensure that your passwords are strong and unique. Avoid using easily guessable information.
- Regularly monitor your bank and credit card accounts for any unauthorized transactions. Early detection of fraudulent activity can minimize damage.
Let’s spot the red flags.
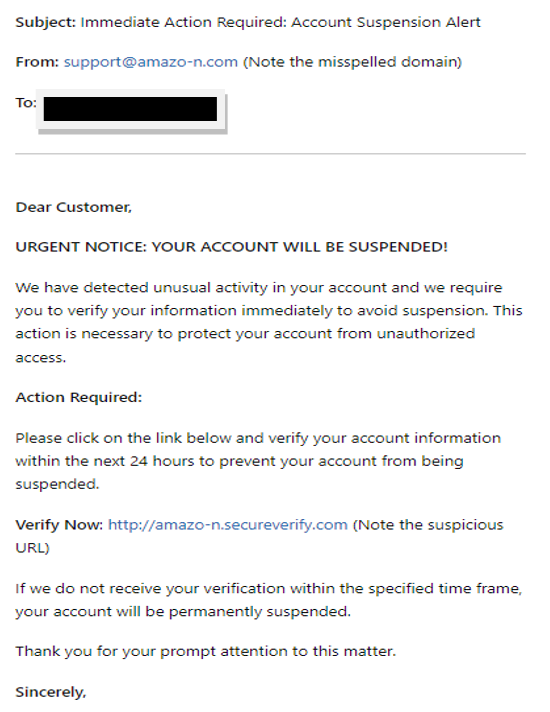
Red Flags.
- Suspicious Sender Email: The email is sent from "support@amazo-n.com" instead of a legitimate Amazon email address like "support@amazon.com".
- Generic Greeting: The email addresses you as "Dear Customer" instead of using your actual name, which legitimate companies typically do.
- Urgency and Threats: The subject and body of the email creates a sense of urgency and fear by threatening account suspension if you don't act immediately.
- Unusual Request: Legitimate companies rarely ask you to verify your account information via email. This is a common tactic used in phishing attacks.
- Suspicious URL: The link provided ("http://amazo-n.secureverify.com") does not lead to an official Amazon website. Hovering over the link reveals the actual URL, which is different from the legitimate website.
- Poor Grammar and Spelling: Although not evident in this example, many phishing emails contain noticeable grammar and spelling errors.
- Generic Sign-Off: The email ends with "Amazon Security Team" instead of a specific name or contact information.
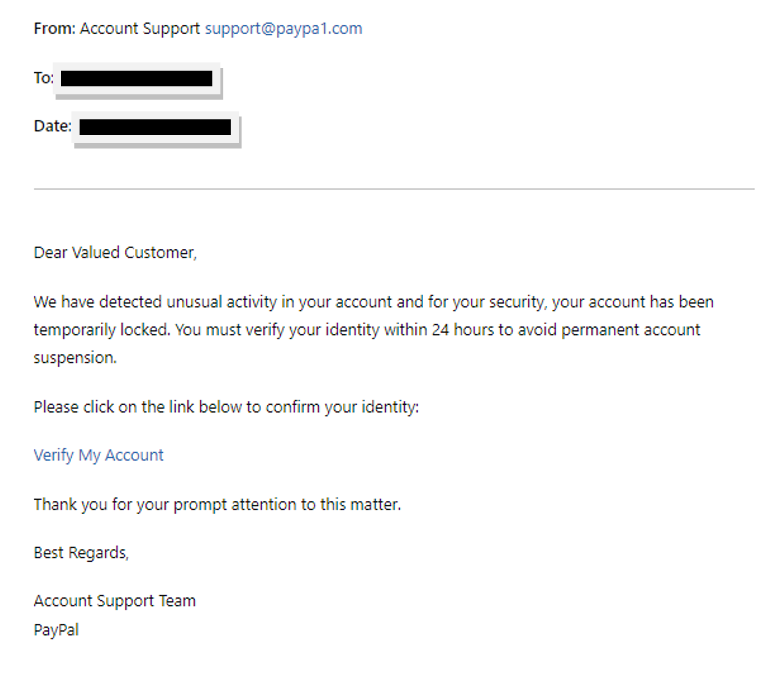
Red Flags
- Generic Greeting: The email uses "Dear Valued Customer," instead of addressing the recipient by name, which is common in phishing emails because they are typically sent out in large batches.
- Urgency and Threats: The email creates a false sense of urgency by claiming that the account has been temporarily locked and requires immediate action. The 24-hour deadline to avoid "permanent account suspension" pressures the recipient to act hastily, which is a tactic designed to prevent thoughtful consideration.
- Spoofed Sender Address: The sender’s email address is "support@paypa1.com." The slight misspelling (using a '1' instead of an 'l') is a common trick used in phishing to make the email address appear legitimate at a glance.
- Suspicious Link: The link provided in the email has a misleading URL. While it appears to be related to PayPal at a quick glance, the domain "paypa1-secure.com" is not a legitimate PayPal domain. Hovering over the link (without clicking) would show the URL, which does not match the expected URL format for the genuine PayPal site.
- Lack of Personalized Information: The email does not include any personal information like the user's name or part of the account number, which legitimate communication from service providers often includes.
- Language and Tone: The use of excessive formalities like "Best Regards" and somewhat stilted language can be a red flag, though not as significant as others. It may sometimes indicate non-native language use, which can be common in phishing attempts, though it's not always a reliable indicator.
Conclusion
Phishing attacks continue to pose a serious threat, yet with appropriate strategies and tools, both individuals and organizations can shield themselves. Recognizing phishing emails, enforcing stringent security protocols, educating users, and deploying sophisticated email security solutions are key to staying one step ahead of cybercriminals. It's crucial to remain alert, proactive, and dedicated to robust email security practices to protect critical information and uphold the integrity of digital communications. Remain informed, exercise caution, and prioritize safety in the digital realm.
CyberSavvy Team.












Thanks. Very detailed.
Posted at May 27, 2024, 9:38 a.m.